Security
Security is one of the most important elements of any businesses IT infrastructure. However, it is usually one of the most neglected elements, that is, until its too late!
Assyst Solutions offer a broad range of security solutions, from physical security, storage security, perimeter security & firewalls, server & desktop antivirus, antispam, encryption, mobile device security.
Perimeter Security - Firewalls & DMZs
A firewall is protective barrier between your business network, and the rest of the outside world. When you connect to the internet you expose yourself to any number of threats. The idea of a firewall is to close off the exposed ports that you're not using. If you don't, then your open ports are an invitation to others to raid your business systems, install trojans, viruses & worms and bombard you with popup messages!
Unless your computer is totally disconnected from the outside world, a firewall is a must have!
Types of Firewall & How They Work
There are two different types of firewall. The first is a personal firewall, this protects a single client, which can be a desktop, laptop or server, and is usually a piece of software installed along side the operating system & other applications. It protects the client from any threats on the local network, or wider internet. The second type of firewall is a corporate/internet gateway. This sits on the perimeter of your network and protects the whole of your internal network from threats on the internet, and can also be used to block traffic from your internal network from reaching the internet, such as instant messaging applications like MSN or Yahoo chat, or for blocking users from social networking sites, such as facebook & myspace. Corporate/internet gateways can be dedicated servers with specialized firewall software installed, or hardware, and are used solely for the purpose of protecting your internal network.
Which Should You Use?
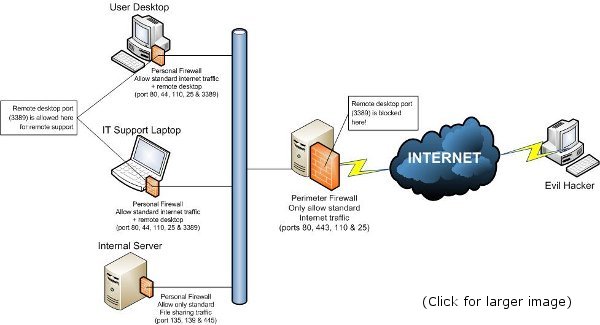
At Assyst Solutions, we believe in 'defence in depth', that is to say, you should be using both personal & corporate firewalls for maximum security.
See the below diagram for an example of 'defence in depth'.
Symantec Endpoint Protection
Symantec Endpoint Protection Small Business Edition provides easy-to-use, enterprise-level protection that optimizes performance and system resources so small businesses can get up and running quickly. It is designed for small business customers who want comprehensive protection that is simple and straightforward to install, deploy, and manage. The streamlined management user interface and easy-to-follow wizards help simplify deployment as well as reduce the need for any specialized training. Pre-configured notifications and automatic security reporting make this a "ready-to-go" product, saving businesses both time and money. Symantec Endpoint Protection Small Business Edition also provides the fastest boot time in the industry1 and the lowest overhead when it comes to everyday interaction with files and applications. Small businesses can now have confidence in their security and focus on running and growing their business.
For the Symantec Endpoint Protection Small Business Edition data sheet Click Here
Symantec Endpoint Protection Enterprise Edition is intended for larger businesses (100+ users) and provides advanced endpoint protection with Symantec Endpoint Protection, Symantec Network Access Control Self Enforcement, Antivirus for Linux, Antivirus for Windows Mobile, security for Domino mail servers, Brightmail Gateway along with all the protection in the Small Business Edition.
For the Symantec Endpoint Protection Enterprise Edition data sheet Click Here
Symantec Protection Suite
Symantec Protection Suite Small Business Edition is designed for businesses with under 100 users who desire a comprehensive yet easy to use security, backup and recovery solution.
The Small Business Edition is an easy to-use, "all-in-one" suite that secures your critical business assets and information against today's complex malware and spam threats, and rapidly recovers data or computer systems. It includes award-winning technologies from the market-leading endpoint security, messaging security, and backup and recovery vendor. Symantec Protection Suite Small Business Edition provides multiple layers of protection with unmatched defense against email-borne threats and security risks. This all-inclusive suite creates a secure environment where computer system failures, malware, and spam risks are accurately identified and addressed immediately. Symantec Protection Suite Small Business Edition also enables reliable recovery of data in seconds or complete systems in minutes, ensuring high availability and avoiding business-interruption threats.
For the Symantec Protection Suite Small Business Edition data sheet Click Here
Symantec Protection Suite Enterprise Edition is designed for larger businesses with over 100 users, creating a protected endpoint and messaging environment that is quickly recoverable in the event of a failure.
Symantec Protection Suite Enterprise Edition creates a protected endpoint, messaging, and web environment that is secure against today's complex malware, data loss and spam threats, and is quickly recoverable in the event of failure. Reduce the cost of securing your environment and more effectively manage the inherent risks of today's IT infrastructures with Symantec's market-leading technologies.
For the Symantec Protection Suite Enterprise Edition data sheet Click Here
Which Endpoint Security product is right for me? Click Here
Microsoft Forefront Threat Management Gateway 2010
Microsoft Forefront Threat Management Gateway (TMG) 2010 is the replacement for Microsoft Internet Security and Acceleration (ISA) Server 2006. Forefront Threat Management Gateway allows employees to safely and productively use the Internet without worrying about malware and other threats. It provides multiple layers of continuously updated protections against the latest Web-based threats, including URL filtering, antimalware inspection, and intrusion prevention. These technologies are integrated with core network protection features to create a unified, easy-to-manage gateway that reduces the cost and complexity of Web security. Forefront TMG enables organizations to perform highly accurate Web security enforcement by stopping employee access to dangerous sites based on reputation information from multiple Web security vendors and the technology that protects Internet Explorer 8 users against malware and phishing sites.
Below is a list of just some of the improvements & features included in Threat Management Gateway (TMG) 2010
- Destination URLs are examined for compliance with corporate policy and for malicious potential of destination Web site.
- Inbound and outbound Web traffic is inspected for viruses and malware, including archived folders.
- Enhanced Voice over IP support.
- Forefront TMG provides access control and protection on three layers: packet filtering, stateful inspection, and application layer filtering.
- Remote users can access Exchange Server using the full Outlook MAPI client over the Internet without establishing a VPN connection.
- Simple Outlook Web Access and Microsoft Office SharePoint Server publishing.
- Highly secure publishing of Web servers, internal servers, and Terminal Services.
Assyst Solutions have over 5 years of experience configuring Microsoft ISA Server 2004/2006, and the latest Forefront Threat Management Gateway 2010.
Encryption & Mobile Device Security
Information is one of the most important assets of any company. Whether that's confidential company strategies, or client contact information, it is important for companies to protect their information assets and comply with strict privacy regulations.
With data breaches on the rise, and with increased laptop proliferation, more and more sensitive and valuable data, such as confidential plans and client information, is carried around by employees. The protection of sensitive data, especially in mobile computing, is more important than ever.
Mobile workforces expose a huge amount of company information outside the secure office perimeter. Without strong data protection this sensitive information is at risk from corporate espionage, accidental loss, or casual theft. Sensitive information landing in the wrong hands can result in significant financial loss, as well as media coverage of data breaches seriously damaging corporate reputations. And privacy regulations around the world can open enterprises to civil litigation and criminal prosecution.
If a mobile device does not have adequate protection, a thief could:
- Boot a PC using an external medium like a CD or USB memory stick and access all the saved data without activating the operating system's access controls.
- Find confidential documents and information and either use it themselves or sell it to a third party.
- Use the PC or data medium to import undesirable data and sneak in harmful programs like Trojans or viruses that then compromise system stability.
It's not just external threats that companies have to protect against. A company's own employees can pose a significant risk to corporate information. Only 10 years ago it would have been near impossible to walk out of the office unnoticed with a large number of confidential client files, business plans or sales data. But with the advances in the ways in which we store and exchange information, large amounts of sensitive information can be copied in a matter of seconds onto a USB stick or e-mailed to an external e-mail address.
Without adequate protection, you leave yourself open to:
- A disgruntled employee stealing sensitive information and selling it to competitors.
- An employee removing sensitive information and losing it.
- An unwitting employee plugging in an unauthorized device infected with a virus or other malware.
Assyst Solutions have a vast experience of mobile device security, including hard drive encryption, both internal and removable, and USB device control, allowing you to manage what USB devices are allowed on your network, and who has access to those devices.
Restrict, Monitor & Report Internet Access
As the internet has grown, and become an increasingly important communications tool for most companies, it has also introduced a number of problems for employees. Problems range from unproductive personal internet use and bandwidth hogging, to the more serious threat of downloading and introducing viruses, and other malware into the corporate network.
It is believed that 44% of workers with web access spend an average of 3 hours per week (a little over 30 minutes per day) using it for non-work related purposes. This amounts to 150 hours a year, per employee. A company with 50 employees, on an average wage of £10 per hour, could be potentially losing £75,000 a year, to non work related surfing!
Assyst Solutions can offer a simple solution to a serious problem! Our 'best of breed' Internet Blocking and Filtering Solution offers all of the following features, for a one time license fee - no annual or monthly subscription::
- URL allow & block lists
- Deny internet access altogether
- Internet access scheduler - so you can allow internet during lunch hours
- Timed internet access - so an individual user, or group that needs full internet access can be given access for a set period of time only
- Content filtering - restrict the downloading of unauthorised file types
- Application blocker - so you can block/restrict applications such as games or chat programs
- Device blocker - so you can block access to cdrom, floppy or usb devices
- Remotely lock computers
- Remotely shutdown or reboot computers
- Import users from active directory
- Create multiple groups of users each with custom policies
- Apply different policies to different groups
- Apply policies to individual users
- Policies can be enforced offsite, (for roaming/mobile laptop users)
Application & Device Blocking
In a society where the use of portable storage devices and removable media is commonplace, the threat that these devices pose to organizations is often ignored. Devices such as USB keys, MP3 Players, iPods, and mobile phones are connecting seamlessly to the corporate network, leaving company confidential information exposed.
Although the majority of workers are hard working, some employees have a 'do as little as possible' attitude. They may waste precious time by running dangerous, time-wasting or nuisance applications such as KaZaa, MSN, instant-messaging programs or games.
Both of these problems can be bad news for you business for a variety of reasons:
- Loss of confidential information can leave organizations open to civil litigation and criminal prosecution
- Loss of confidential information can result in a damaged reputation and loss of customer trust
- Distracts employees and reduces productivity
- Costs your business for unproductive time
- Time wasting employees will waste your company resources, i.e. downloading music or software through your corporate internet connection
- Downloading or viewing of objectionable or offensive material through your corporate internet connection can make your business liable under law
- Increases risk of introducing viruses, trojans, or other malware to your organization's network
Obviously, it is no longer possible to assess the productivity of employees by simply walking around the office and checking whether they are still sitting at their workstations.
Assyst Solutions have a solution to both problems! We can provide a 'best of breed' application & device blocker, that will enable an organization's administrator to quickly and easily block users from running dangerous, time-wasting or nuisance applications, as well as block unapproved devices, such as USB keys and MP3 players.
Our solution isn't just aimed at corporate environments; our application & device blocker will also benefit schools, where it can restrict students from launching unauthorized applications (such as games) during class.
For details on how we can assyst your business call us on:
Tel: 0845 241 66 11
Mobile: 07584 133 087
Click here to send us an email
|



